Help page about Account Privilege Manager.
summary
The Account Privilege Manager is the most powerful of TROCCO's privileges.
Only one user can be granted per account, and multiple users cannot be granted.
The privileges of the user you will receive when your account is first issued will be Account Privilege Administrator.
Account Privilege Manager can
The account privileged administrator can view and operate the following in addition to being able to do the account administrator privileges.
Deleting Users
The account privileged administrator can delete users.
For more information, see Deleting Users.
View and manipulate all resources created in your account
Account Privileged Administrators can view and manipulate all resources created in the account, including ETL Configuration and Data Mart Configuration.
Normally, TROCCO only allows you to view, execute, edit, delete, and perform other operations on the resources that you have created.
If you are using the team function, in addition to the above, you can also perform various operations on resources that you have not created based on the roles assigned to the team to which you belong.
In other words, TROCCO generally does not allow any operations on resources to which it does not have authority.
However, only the account privileged administrator may exceptionally perform all operations (read, edit, execute, and delete) on all resources that exist in the account.
Deleting a user does not delete resources created by that user, such as ETL Configurations and Data Mart Configurations.
If the resource is not managed by a Resource Group, it is usually not available for operation.
However, an account privileged administrator can operate even such a resource.
View and manipulate all Team Resource Groups created in your account
When the Teams feature is enabled, the account privileged administrator can view and manipulate all Team Resource Groups created in the account.
You can also select a Resource Group on the edit screen for each resource, and at this time, you can choose where the resource belongs from all the Resource Groups created in your account.
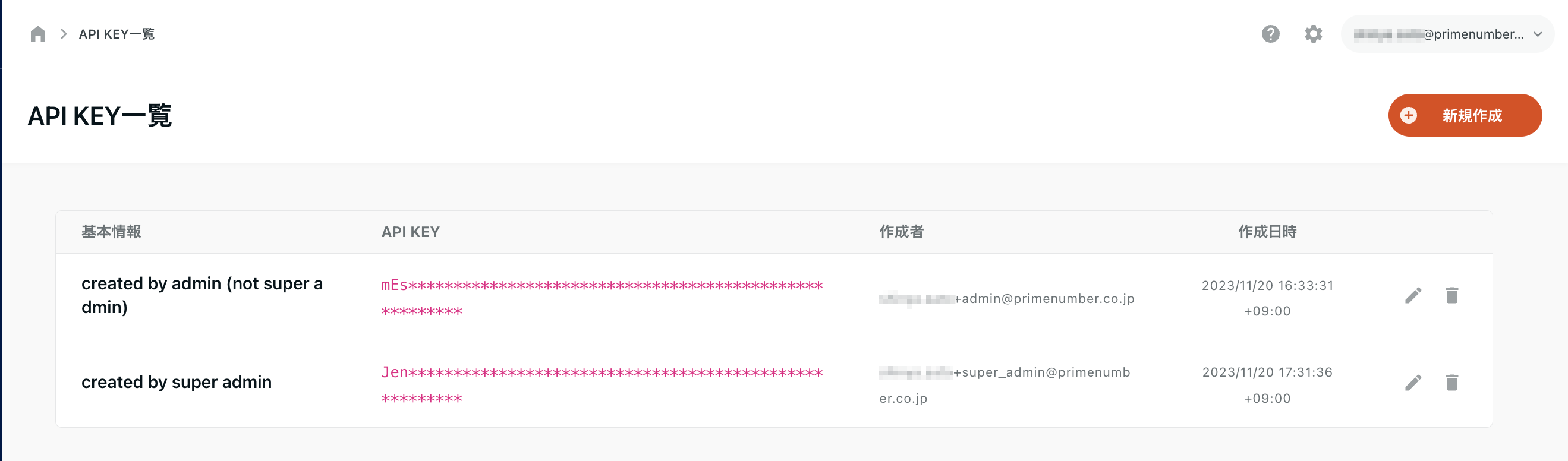
View and manipulate all API Keys created in your account
The account privileged administrator can view, edit, and delete all API Keys created in the account.
For more information about API KEY, see About TROCCO API.
The value of API Key can be checked only immediately after creation.
After that, the API KEY is masked except for the first three characters of the API KEY.
Therefore, even the account administrator cannot check the specific value of API Key.
Change of organization name
The account privileged administrator can change the organization name.
See organization name for details.
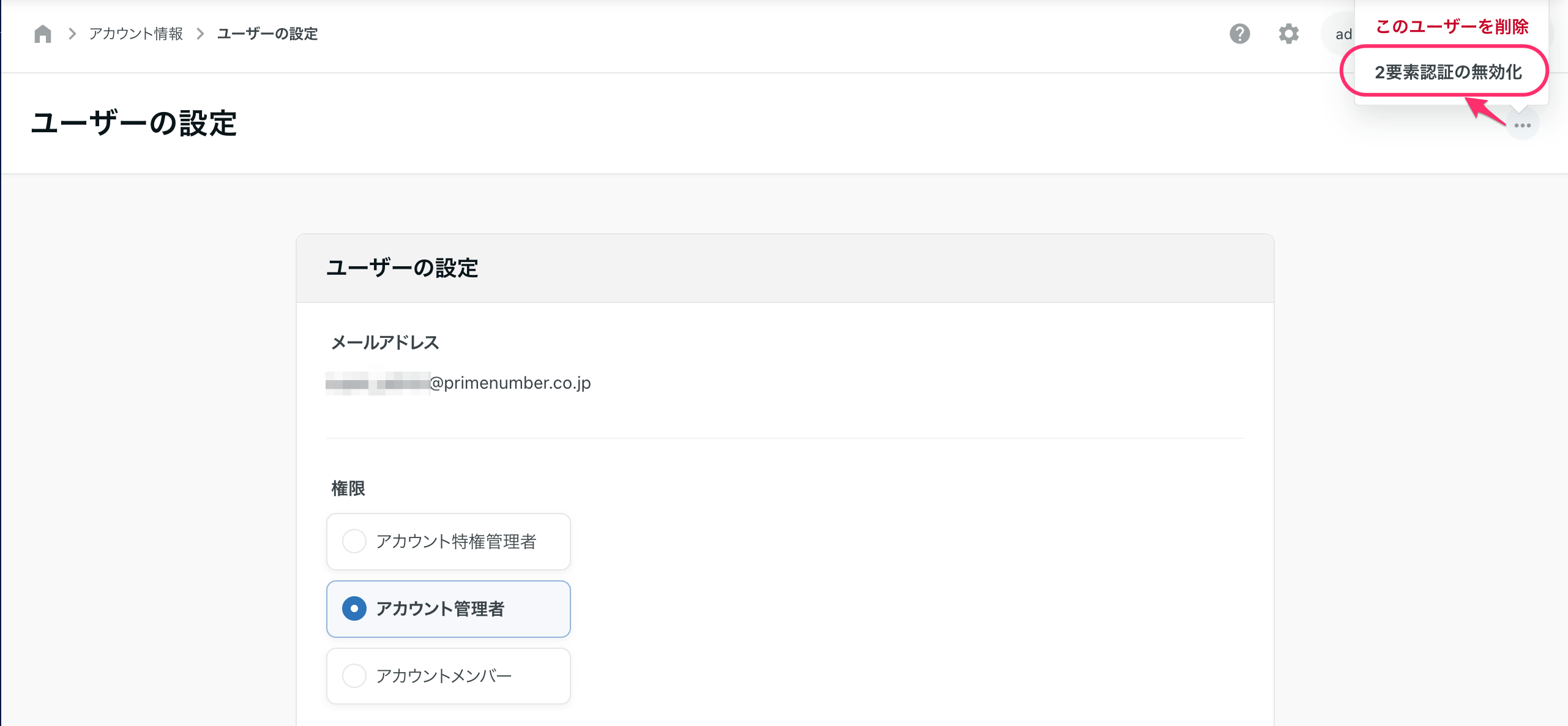
Disable two-factor authentication set by each user in the account
Disabling two-factor authentication is an operation that is not originally recommended because it reduces the level of security.
It is recommended that deactivation be limited to cases where a user is no longer able to log in using two-factor authentication.
Users who have successfully logged in by disabling it should be prompted to enable two-factor authentication again.
The account privilege administrator can disable the two-factor authentication set by each user in the account.
It can be disabled from the user's permission settings.
Delegation of Account Privilege Manager Authority
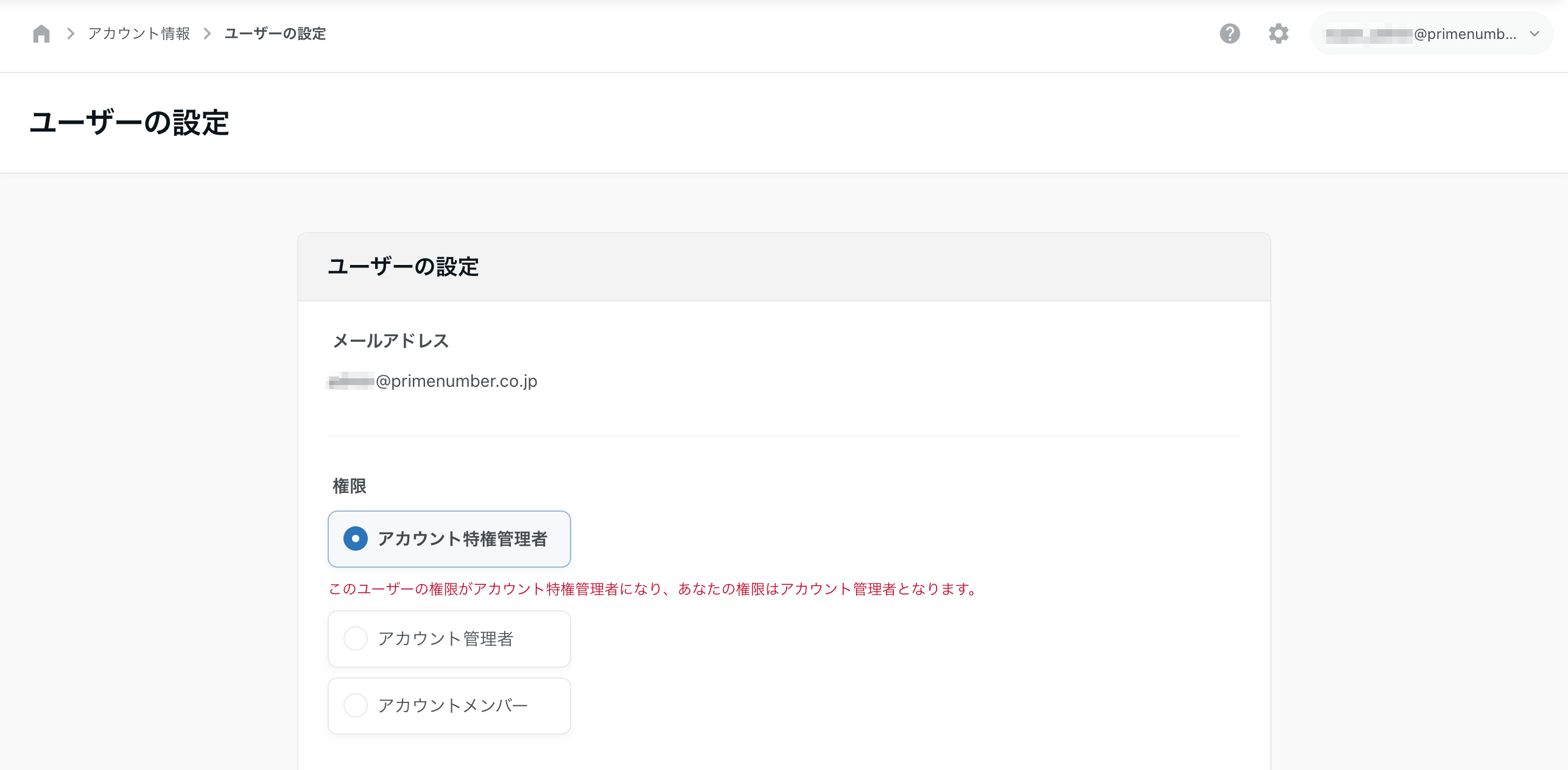
Account Privilege Administrator privileges can only be granted to one user per account.
More than one user cannot be an account privileged administrator.
In addition, no changes can be made that would result in zero account privileged administrators in the account.
Therefore, when changing the account privilege manager, the existing account privilege manager must delegate authority to another user.
Delegation of account privileged administrator privileges can only be done by the account privileged administrator himself/herself.
delegation procedure
-
From the User Management screen, click Edit for the user to whom you want to delegate privileges.
-
Select Account Privilege Manager from Privileges
-
Check the Delegate account privileges administrator checkbox in the warning at the bottom of the screen .
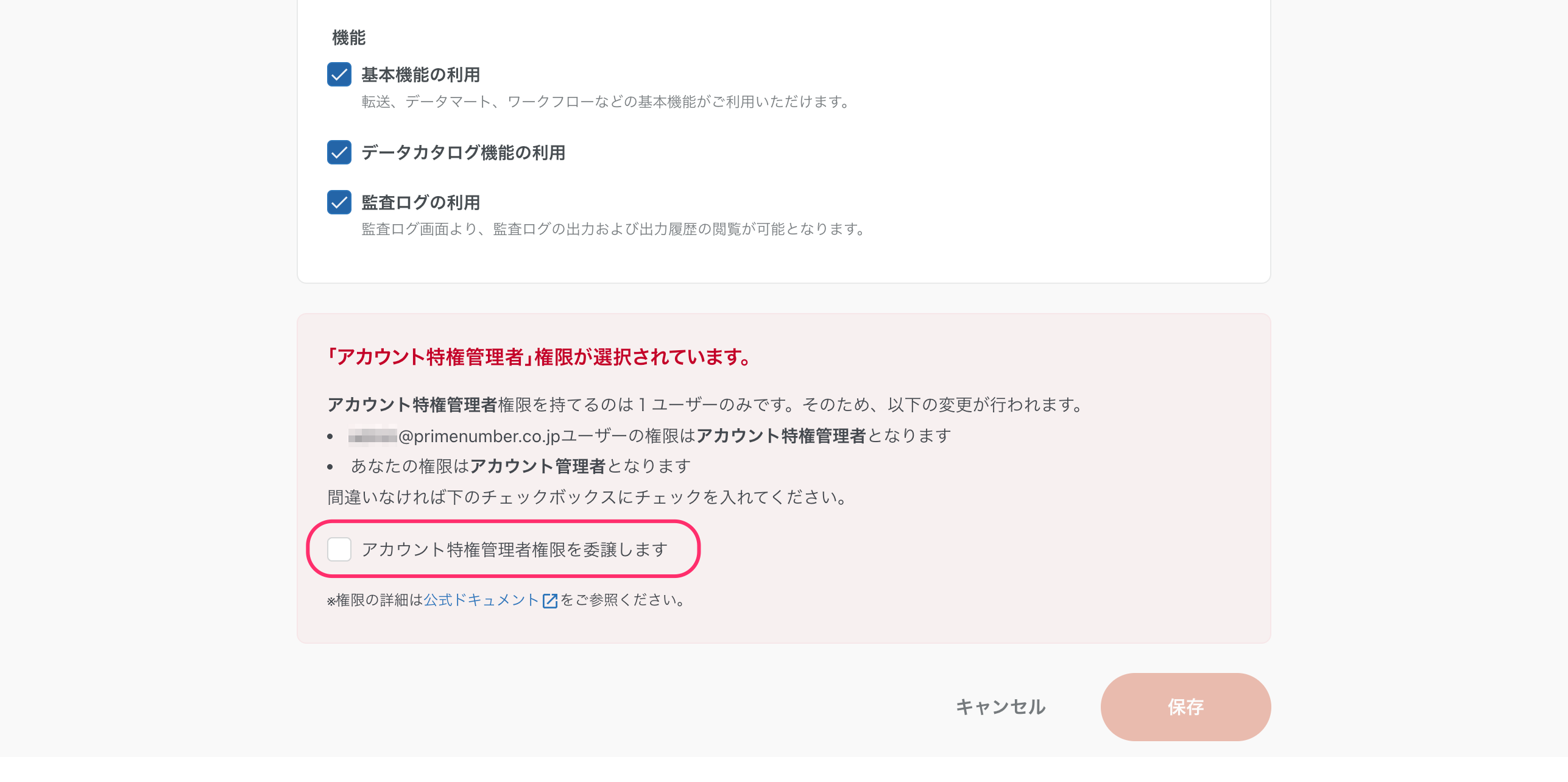
-
Click Save
Authority is delegated immediately upon clicking Save.
In the unlikely event that you have unintentionally delegated account privileged administrator privileges, please ask the account privileged administrator to whom you delegated the privileges to redelegate the privileges.