summary
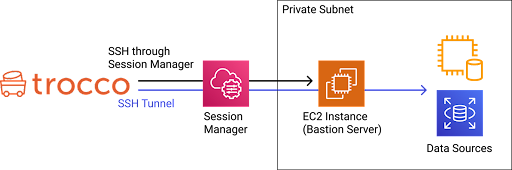
By creating an SSH tunnel between TROCCO and a customer-provided server via AWS Systems Manager Session Manager, the customer can connect to the data source via a trestle server in a private subnet.
Compared to the usual SSH tunnel connection, TROCCO can be used more securely because it eliminates the need to place the stepping-stone server on a public subnet.
The following is a schematic diagram of the connection using AWS Systems Manager Session Manager (hereafter simply referred to as Session Manager).
To do this, after creating the Session Manager Connection Configuration, select the Session Manager Connection Configuration you wish to use from the Data Source Connection Configuration.
As of 02/2024, only MySQL and PostgreSQL are supported.
For more information about Sesesion Manager, please see the following AWS documentation
AWS Systems ManagerSession Manager - AWS Systems Manager
constraints
It cannot be used in conjunction with a connection using the SSH tunnel.
Prerequisite.
The following items must be performed on your AWS account
Note that these are the minimum settings required to use Session Manager with TROCCO.
Please modify it to match your organization's policy.
Create an instance to serve as a stepping stone server
- SSM Agent must be installed on the instance
Please refer to the AWS documentation for installation instructions.
Using SSM Agent - AWS Systems Manager
Configure IAM instance profiles to allow Session Manager connections to the stepping stone server
- Attach the AWS management policy AmazonSSMMManagedInstanceCore to the instance.
- Alternatively, please refer to the AWS documentation to set it up.
Verify or create an IAM instance profile using Session Manager permissions - AWS Systems Manager Session Manager
Configure IAM policy to allow Session Manager connections to the stepping stone server
- Create an IAM policy with reference to "End User Policies > Session Manager and CLI" on the following page and attach it to the IAM user to be used with TROCCO.
- Quick Start Default IAM Policy Session Manager - AWS Systems Manager Session Manager
- To start a session using SSH, go to
"Action":. ["ssm:StartSession"]``Resourceshould be set todocument/AWS-StartSSHSessioninstead ofdocument/SSM-SessionManagerRunShell.
- The following is an example of an IAM policy to grant minimum privileges. Please refer to this page for reference.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "ssm:StartSession" ], "Resource": [ "arn:aws:ec2:<REGION>:<ACCOUNT-ID>:instance/<INSTANCE-ID>", "arn:aws:ssm:*:*:document/AWS-StartSSHSession" ], "Condition": { "BoolIfExists": { "ssm:SessionDocumentAccessCheck": "true" } } } ]
}
## Setup Method
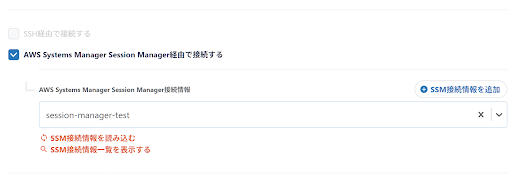
On the Create/Edit Connection Configuration screen below, enable the **option to connect via AWS Systems Manager Session Manager**.
- MySQL Connection Configuration
- PostgreSQL Connection Configuration
If you wish to create a new AWS Systems **Manager** Session Manager Connection Configuration, click **Add SSM Connection Configuration**.
If you wish to review the AWS Systems Manager Session Manager Connection Configuration you have already created, click **View SSM Connection Configuration List**.
{height="" width=""}
## entry
This section describes the input items required to create a Session Manager Connection Configuration.
| Item Name | Required | Default Value | Contents
| --- | --- | --- | --- |
| Name | Yes | - | Enter the name of the Connection Configuration to be used inside TROCCO. | Yes
| Memo | No | - | Enter a memo for Connection Configuration to be used inside TROCCO. | No | - | Enter a note of connection information to be used inside TROCCO.
| AWS Access Key ID | Yes | - | Enter the AWS Access Key ID to use Session Manager. | Yes | - | Enter the AWS access key ID to use Session Manager.
| AWS Secret Access Key | Yes | - | Enter the AWS Secret Access Key to use Session Manager. | Yes | Yes
| AWS Region | Yes | ap-northeast-1 | Please enter the region where you will use Session Manager. | Yes | ap-northeast-1
| EC2 Instance ID | Yes | - | Enter the instance ID of the EC2 instance that will be used as a stepping stone when using Session Manager.<br>The instance ID is a string beginning with i- or mi-. |.
| SSH Port | Yes | 22 | Enter the port for SSH connection to the EC2 instance that will be used as a stepping stone when using Session Manager. | Yes
| SSH user | Yes | ec2-user | Enter the user name for SSH connection to the EC2 instance that will be used as a stepping stone when using Session Manager. | Yes
| SSH Private Key | Yes | - | Enter the private key file to connect to the EC2 instance that will be used as a stepping stone when connecting using Session Manager.<br>Generally, this will be the private key of the key pair selected or created when the EC2 instance is created. | (default)
| No | - | SSH private key passphrase | No | - | Enter SSH private key passphrase if you have one. | No | - | SSH private key passphrase, if any
## supplement
#### The SSH tunnel through Session Manager is set up before the transfer and closed after the transfer is complete.
* The session remains on Session Manager, but is closed after 20 minutes by default.
To change the amount of time before the session is closed after completion, please refer to the following document
[Specify the timeout value for idle sessions. - AWS Systems Manager](https://docs.aws.amazon.com/ja_jp/systems-manager/latest/userguide/session-preferences-timeout.html)
* The maximum connection time of the Session Manager session itself can also be set.
The setting is recommended to avoid the session remaining for some reason.
For more information, see [Specifying the Maximum Session Time - AWS Systems Manager](https://docs.aws.amazon.com/ja_jp/systems-manager/latest/userguide/session-preferences-max-timeout.html).
#### Since the transfer execution environment is isolated, Session Manager sessions and SSH tunnels are not shared between customers.
#### If the connection fails, please try connecting from your environment.
* Install the AWS CLI and Session Manager plug-in in your environment.
[Install, update, and uninstall AWS CLI version 2 - AWS Command Line Interface](https://docs.aws.amazon.com/ja_jp/cli/latest/userguide/install-cliv2.html)
[-Install the Session Manager plugin for the AWS CLI - AWS Systems Manager Session Manager](https://docs.aws.amazon.com/ja_jp/systems-manager/latest/userguide/session-manager-working-with-install-plugin.html)
* Create a profile for the connection you wish to verify.
[Configuring configuration and credentials files - AWS Command Line Interface](https://docs.aws.amazon.com/ja_jp/cli/latest/userguide/cli-configure-files.html)
* Please try executing the following commands
・`aws ssm start-session --target <bastion instance ID> --profile <your profile> --document-name AWS-StartSSHSession`
If a message starting with **"Starting session with SessionId"** is displayed, the connection is established.
If you are unable to connect from your environment, please review the settings on AWS with reference to the error message output.
If you are able to connect from your environment, please make sure that you have entered the correct information into TROCCO.
If the connection from TROCCO continues to fail, please contact support.